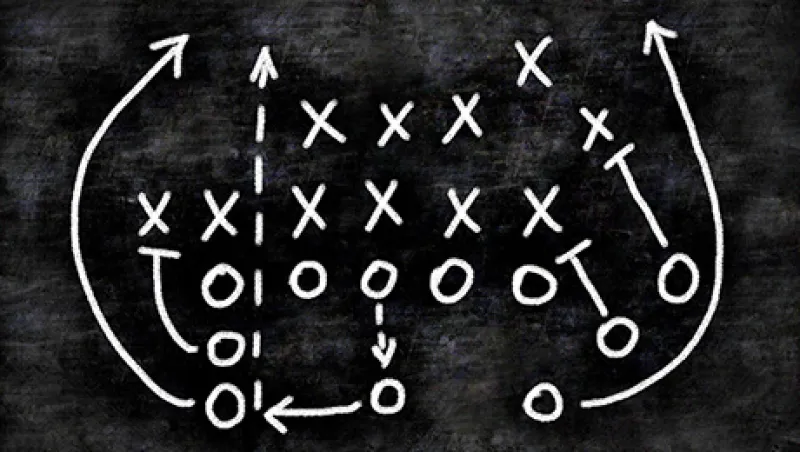There is an adage, often invoked in sports, that the best defense is a good offense. Control the ball or the pace of the game, and your opponent can’t do the same. The idea applies in many contexts — corporate, political, military and, as is becoming more and more apparent, cybersecurity. So powerful and persistent are hacking and malware threats that strategists are questioning the wisdom of maintaining a purely defensive posture.
In other words, maybe it is time to inject some offense into cyberstrategy. It is a delicate subject.
Attack mode is accepted as an option in national security policy — as well it should be, to counter offensive capabilities of major (China and Russia, for example) and lesser (Iran, North Korea, ISIS) powers around the globe. But this is not conventional warfare. Those who have the funding and motivation to control the cyberattack initiative, including the nation-states and rogue actors that the U.S. Cyber Command keeps in its sights, are targeting private sector corporations and infrastructure. There is only so much that military and law enforcement entities can do. The biggest banks are spending hundreds of millions of dollars a year on cybersecurity and have to assume that the cost of repelling attacks will only get steeper over time.
Lawyers and information security experts — among them Stewart Baker, a Washington-based partner of Steptoe & Johnson and a former National Security Agency general counsel — say the private sector needs leeway to take some matters into its own hands. But direct attacks, or even a retaliatory “hacking back,” are illegal under the Computer Fraud and Abuse Act of 1986. And vigilante justice, if not universally repugnant, doesn’t make for good diplomacy.
“I am aware of an American company that saw data stolen from it on a foreign server,” retired Air Force general Michael Hayden, who was director of both the NSA and the Central Intelligence Agency, said in a recent presentation to a gathering sponsored by identity technology company Centrify Corp. “Their lawyer said, ‘You can’t go get it.’”
A somewhat less “offensive” concept is making headway in policy circles. Active defense is defined by Frank Cilluffo, director of the George Washington University Center for Cyber & Homeland Security, as “the use of proactive measures by U.S. companies to defend themselves and their most critical assets against sophisticated and determined cyber adversaries.”
Hayden, now a principal of consulting firm Chertoff Group, acknowledged the active defense point of view that “where we are is too restrictive, and the private sector should be given more space to defend itself beyond the firewall” — though he cautioned against running afoul of the Computer Fraud and Abuse Act.
One recommendation of “An American Strategy for Cyberspace,” a paper published in June by the American Enterprise Institute, is to “empower the private sector to more effectively defend itself” and explore the feasibility of such tactics as turning aside incoming attacks, improving information sharing with government agencies and corporate peers and retrieving stolen information. It added that “the U.S. should consider reforming the Computer Fraud and Abuse Act to clarify and perhaps in limited ways expand private companies’ ability to engage in active defense.”
Cilluffo said in congressional testimony in February that “at a minimum it is the responsibility of the U.S. government to delineate an operating framework [for the private sector] to engage in active defense.” A task force formed by his center at GWU expects to issue a report on the subject this year.
Indeed, active defense is more nuanced than direct hacking, and some measures do not require legislation, says Ertem Osmanoglu, cybersecurity and risk management executive of consulting firm Ernst & Young. These include “introducing complexity into the environment” in a way that prevents or deters intrusions; and attribution techniques that geolocate and yield other intelligence for identifying adversaries.
“Organizations today require a dynamic solution that hunts for adversaries in real time and eliminates them,” Vikram Desai, security lead of Accenture Analytics has said. In March the firm announced an alliance with and strategic investment in Endgame, a cybersecurity company that says its systems “allow organizations to move from being the hunted to being the hunter.”